FTPRush (formerly known as “UltraFXP”) is a popular closed-source freeware FTP Client for Windows and comes with some handy features.
If the user chooses to store site passwords FTPRush applies some cryptography to the plaintext password before writing it to RushSite.xml. In this post I will explain in detail the key setup, algorithm and mode of operation utilized. The source code of a sample implementation is available for download.
The RushSite.xml file holds all account data like IP, port, protocol, username, encrypted password, etc. FTPRush offers the user to encrypt the whole RushSite.xml file with a user-defined password via a non-disclosed algorithm. This might be covered in one of my later posts.
Key setup & algorithm
char secret[16] = "th3m3ugaysshit9";
char IV_init[8] = {
0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff
};
The “secret” string “th3m3ugaysshit9” is being hashed using RIPEMD-256. The output digest serves as the key to a default 16 round blowfish algorithm. Next IV_init is encrypted once through blowfish in ECB mode to yield the 8 byte IV which is used as an initialization vector for the mode of operation. IV itself gets encrypted again by blowfish in ECB mode and the result is stored to IV_short (see short passwords).
// both vectors and key are constant as the "secret"
// from which they are derived is constant as well
char key[32] = {
0xb4, 0xe8, 0xd1, 0x6c, 0x26, 0x32, 0x3d, 0x4a,
0xea, 0x80, 0x26, 0xcd, 0xce, 0xbf, 0xfe, 0x6a,
0x4a, 0xe2, 0x7d, 0xeb, 0x77, 0xf0, 0x89, 0x4c,
0xbc, 0x25, 0xfa, 0x03, 0xe0, 0x1b, 0x6b, 0x1c
};
char IV[8] = {
0x3b, 0xc5, 0x1f, 0x5a, 0x5e, 0x96, 0x13, 0x45
};
char IV_short[8] = {
0x2b, 0x74, 0x73, 0xd3, 0x99, 0x49, 0x10, 0x55
};
Short passwords
For passwords less than 8 characters FTPRush performs an XOR operation on the password with IV_short until it reaches the end of the password. The result is directly written to disk. Note that for short passwords the blowfish encryption does not add any security as it is merely used for key derivation purposes and IV_short is always the same due to the constant “secret” char array.
Longer passwords & mode of operation
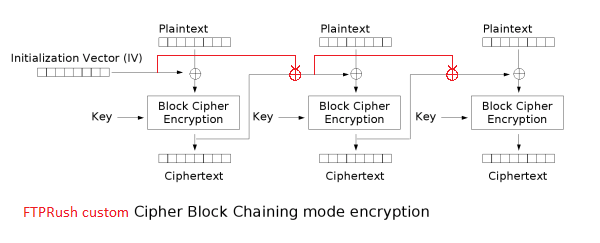
Plaintext passwords with at least 8 characters are encrypted by FTPRush with the blowfish algorithm in a custom CBC mode as shown below (modifications drawn red). The author obviously used the Delphi library “delphidec” for all the crypto stuff. As I could not find an old version of that library I cannot tell whether this mode was a feature from the library authors or a bugged CBC implementation. At least the current library (version 5.2 as of writing this blog entry) does not offer such a mode. I am not an expert in cryptography so I have no idea if this modification enhances or weakens the cryptographic stength. Maybe it was just added by the UltraFXP/FTPRush authors for obscurity reasons. If anyone knows more about this I would love to hear from you.
If password’s length is not a multiple of 8 FTPRush then takes the feedback from the last custom CBC block and encrypts it by blowfish in ECB mode. I called the result IV_modulus. IV_modulus is then XOR’ed with last bytes of the plaintext password. This is the same fashion as for short passwords except that the XOR vector is not constant anymore. The result is written to RushSite.xml as the encrypted site password.
Sample implementation
I have implemented the algorithms used for encryption and decryption in a small C project (vide infra). It uses the crypto library LibTomCrypt v1.17. The source code and the necessary modifications to that library are included as well as a precompiled executable.
Open questions and closing words
- What does the message in the “secret” char array mean?
- Why was a modified CBC employed instead of a normal CBC?
If you have any ideas about that I would love to hear your opinions.
So much for my very first blog entry. I hope you enjoyed reading 🙂
Comments are closed.